###MEMSCAN
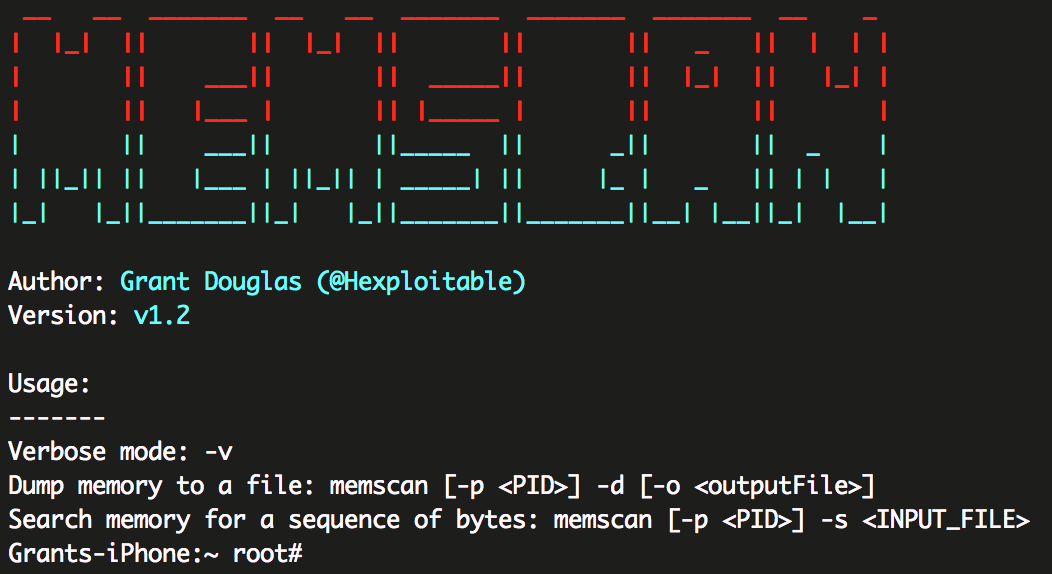
MEMSCAN is a utility for iOS which I’ve been working on in bits and pieces here and there. I wanted to be able to dump the memory of a given process or to search for certain bytes in memory and get back an address for those bytes. This can be particularly useful when you’re testing an application which uses PIE and the symbols are not available. Using this technique you can look up the method fingerprint (e.g the first 16 bytes) and then get the address of the method.
###Using memscan Using MEMSCAN is pretty easy, there are currently two ways you can use the tool.
The first way is to use the -d option which will dump the memory of a given process to an output file in the active directory.
The second way to use memscan is to use the -s flag to specify an input file which contains a sequence of bytes to search for. When storing the bytes in a file, you should do this like so:
echo -n -e '\x55\x48\x89\xE5\xB8\x15\x00\x00\x00\x5D' > hex
###Downloading memscan You can download memscan simply by adding my repo to Cydia: http://grantdouglas.co.uk
The source code for MEMSCAN is now hosted in git: Github.com - Hexploitable/MEMSCAN
###Problems MEMSCAN is what I would classify as beta. For this reason I expect that it will not function properly at all times so if you experience any issues with it, please do get in touch and provide me with some details and I can look into it.
You can contact me either at @Hexploitable on Twitter or via email.
This post has a follow up here.
####Further reading Abusing Mach on Mac OSX pdf